Type ps -ax at Terminal’s command prompt to list every process running, along with additional details such as the PID, the elapsed time running, and the process name and location (shown in the CMD column). Mac OSX - What program is using port 8080. Thank you very much 🙂 Just a suggestion. You wrote down “The name “java” doesn’t tell you anything, to get the detail, ps the java PID 12895 like this:”. Somehow I’ve only noticed now that netstat on Mac OS X cannot show the program name. Actually on Mac OS X, the -p parameter of netstat doesn’t mean program or process but protocol. Also there is no -t parameter but it can be done using -ptcp. $ netstat -an -ptcp grep LISTEN tcp4 0 0 127.0.0.1.10000.
- Some Apple software, including macOS, iOS, and iTunes, uses different ports and servers to connect to various services. ITunes for Windows also installs some processes that run in the background when the software is open.
- Here is how to see what ports are open listening on a server. This is perhaps the most important potential vulnerability. Having ports listenting to outside traffic also takes CPU effort, which consumes electricity and thus reduce battery life. Spotlight on Network Utility to List Ports. Apple’s macOS Spotlight is like Window’s Search omni.
Jun 2 2011
Sometimes, there's a program running on a port and you don't know what it is. How do you find out? I find this happens when I start a webserver up to test something locally and then I forget about it. So, if I wanted to find out what was running on port 80: This command shows a list of open files. The -i option checks for internet addresses with the colon symbol representing a port (instead of an actual IP address). Note, I've only used this on Mac OS X. I'm not sure if there's an equivalent for *nix or if it's available in some package.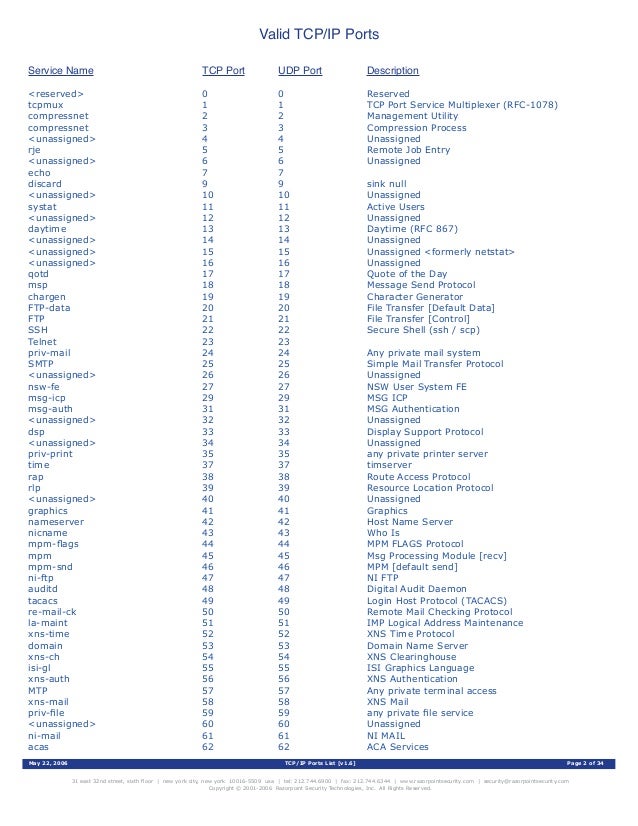
What ports are open for hacking on my Mac and Linux machine?
- Processes Tour
Here is how to see what ports are open listening on a server.
This is perhaps the most important potential vulnerability.
Having ports listenting to outside traffic also takes CPU effort,which consumes electricity and thus reduce battery life.
Spotlight on Network Utility to List Ports
Apple’s macOS Spotlight is like Window’s Search omni-box.*
Press Command+Spacebar.
Type the name of utilities that are buried, such asNetwork Utility.
Click the keyboard return/enter key to launch the Network Utility app.
Select the 'Port Scan' tab.
Enter the IP (such as 127.0.0.1), localhost, or domain name you wish to scan for open ports.
Choose scan to see what ports the server responds to.
List open files = lsof

In a Terminal command line:
PROTIP: If you’ll be using this often, create an alias such as
of.“lsof” is a contraction for “list open files”.Without any options specifications, lsof lists all open files belonging to all active processes.
“-nP” is a combination of “n” for no resolution of IPs to hostnames using DNSand “P” for no resolution of Port names from numbers.
This is because the command already takes several seconds to run.
“+c 15” specifies command width of 15.
Piping to grep filters out only lines containing “LISTEN”.
NOTE: All options are shown by this command:
lsof -h
See http://www.thegeekstuff.com/2012/08/lsof-command-examples
Drag your Terminal window wider to remove word-wrap.
“FD” column lists File Descriptors. “u” is for read and write mode. “r” for read only, “w” for write-only.
Linux requires root on operations for well-known ports below 1024.
Registered Ports: 1024 through 49151.
Dynamic/Private : 49152 through 65535.
TCP (Transmission Control Protocol) is the most commonly used protocol on the Internet and any TCP/IP network. TCP enables two hosts to establish a connection and exchange streams of data. TCP guarantees delivery of data and that packets will be delivered in the same order in which they were sent. Guaranteed communication/delivery is the key difference between TCP and UDP on ort 53.
UDP (Datagram Protocol) is connectionless and does not guarantee reliable communication; it’s up to the application that received the message to process any errors and verify correct delivery. UDP is often used with time-sensitive applications, such as audio/video streaming, where dropping some packets is preferable to waiting for delayed data.
Processes Tour
NOTE: Drag the scroll bar to see what is beyond what is displayed.
mongod is MongoDB listening on port 27017.
I should keep that closed unless I need it.
Macos List Ports For Processing
https://www.mkyong.com/mongodb/mongodb-allow-remote-access/
In Node, close all connections when the app closes completely:
2BUA8C4S2C
When I search for “2BUA8C4S2C” I see “2BUA8C4S2C.com.agilebits” in folder /Users/mac/Library/Group Containers
This says This port is used only on the loopback interface (127.0.0.1) for the 1Password extension to talk to the 1Password Agent. It should be safe to firewall it from any sources other than 127.0.0.1. If you do a packet capture on lo0 and then filter by tcp.port 6258 you can see what traffic is being passed. Nothing is transmitted in the clear.
Skype I don’t mind keeping open. I use it a lot.
Dropbox - why does it need to be kept open?
I’ll use just their web page when I need it.
See https://www.dropbox.com/help/41
Resiliox20Sync I used once to get a file.
In Resilio Preferences, uncheck “Start Resilio Sync on startup”.
SketchMirrorHel
Macos List Ports In Use
XMPP ports 56989 and 56990
For a list of processes on Mac:
http://www.westwind.com/reference/OS-X/background-processes.html
ftp (tftp) should not appear.
Firewall
NMAP
Scan other machines
Install
brew install nmap
There are a lot of options
nmap -h
The format:
nmap [scan type] [options] {target specification}
There are a lot of options
nmap -h
Resources

https://www.wikiwand.com/en/Lsof
https://danielmiessler.com/study/lsof/#gs.3YHJpiA
https://netadmintools.com/html/lsof.man.html
https://www.zeek.orgZeek (formerly Bro) and/or https://www.snort.orgSnortNetwork Intrusion detection systems (NIDS)
https://cybersecurity.att.com/products/ossimAlienVault Open Source SIEM (OSSIM) with Open Threat Exchange (OTX)Security Information and Event Management (SIEM) software
CompTIA CySA+ (CSO-001) exam launched April 21, 2020 on Vue & Pearson online$359 to answer 75% of 85 questions in 165 minutes
VIDEO:
Threat and vulnerability management:
- Explain the importance of threat data and intelligence.
- Given a scenario, utilize threat intelligene to support organizatoinal security.
- Given a scenario, perform vulnerability management activities.
- Given a scenario, analyze the output from common vulnerability assessment tools.
- Explain the threats and vulnerabilities associated with operating in the cloud.
- Given a scenario, implement controls to mitigate attacks and software vulnerabilities.
- Software and systems security
- Given a scenario, apply security solutions for infastructure management
- Explain software assurance best practices
- Explain hardware assurance best practices
- Security operations and monitoring:
- Given a scenario, analyze data as part of security monitoring activities.
- Given a scenario, implement configuration changes to existing controls to improve security.
- Explain the importance of proactive threat hunting.
- Compare and contrast automation concepts and technologies.
- Incident response
- Explain the importance of the incident response process.
- Given a scenario, apply the appropriate incident response procedure.
- Given an incident, analyze potential indicators of compromise.
- Given a scenario, utilize basic digital forensics techniques.
- Compliance and assessment
- Understand the importance of data privacy and protection
- Given a scenario, apply security concepts in support of organizational risk mitigation
- Explain the importance of frameworks, policies, procedures and controls.
More on OSX
This is one of a series on Mac OSX:
Please enable JavaScript to view the comments powered by Disqus.